How far home printing has come in fewer than four decades will astound you
Home printing technology has progressed beyond belief over the past 40 years
Whether you’re an aspiring novelist who goes through reams of paper printing 18 different versions of your latest manuscript, a student racing to finish a last-minute paper, or a design professional fiddling with various layouts for a piece of print collateral, there are a variety of scenarios in which home printing technology is a godsend in our modern day and age.
Today, we take the ability to print documents easily and in the comfort of our own homes for granted. But even as recently as 30 years ago, home printing was considered a luxury — and 50 years ago, it was unheard of.
Below, we dig into the evolution of this highly useful technology, and how it has made its way into our homes and history books.
The advent of home printing
You probably learned about Gutenberg, the printing press, and the birth of commercial printing in school — but the history of home printing is less well-known.
Although some earlier methods of home printing such as silk-screening and phototypesetting existed on a niche basis in the early 20th century, the origins of home printing technology as we think of it today date back to the 1930s. In 1938, American physicist, inventor, and patent attorney Chester Carlson invented the dry printing process, otherwise known as electrophotography or xerography. The six-step process involved exposing photoconductive materials of opposite electrical charges to one another in order to create images when the material was exposed to light.
The fundamentals of this process lay the groundwork for the future of laser printing — although the first laser-integrated printer wouldn’t actually come along until sometime in the 1970s. The first high-speed laser-printer, developed in 1976, hit an impressive (for the time) printing speed of 100 impressions-per-minute. In addition to laser printing, both inkjet printing and dot matrix printing techniques rose to popularity in the 1970s. Most of these devices were so pricey, however, that for the better part of a decade, only businesses could afford to install them.
Printer technology played integral behind-the-scenes roles in history throughout the ‘60s and ‘70s, too: At the 1964 Olympic Games in Tokyo, for example, the “printing timer,” a device that worked by combining time measurement tools with printing functions, was used to gauge results of speed competitions. This piece of technology synchronised pistols, photo-tubes, and photo-finish equipment in order to record and print Olympians’ race times and determine the winners. This technology would later become foundational to the EP101 digital printer, one of the world’s first compact and lightweight digital printers, made by Epson.
It wasn’t until the late 1980s, however, that inkjet printers found a market as a home consumer item — and initial models still cost upwards of $1,000. (The very earliest consumer models cost more than triple that, and boasted just 300 dots per inch — or dpi — resolution.) By the early 1990s, home printing was becoming more common, although resolution was still quite low: One popular model of early ’90s printer advertised 600-by-600dpi resolution, and was considered top-of-the-line for its day.
Epson helped proliferate the popularity of home printing in the 1990s, with its release of machines like the Epson Stylus Color, a 70-dpi color inkjet printer that could produce high-quality photos. In 1997, the company also released the Epson Stylus Photo, a printer that could let people print near-photo-quality images at home.
By today’s standards, though, the printers of the 1980s and 1990s were cumbersome. These machines were massive — some models took up entire industrial-sized desks and weighed as much as 32 kilograms — and printed at a rate of around eight pages per minute (ppm).
As inkjet technology and laser printers continued to advance, the devices became smaller, faster, more manageable, and, as a result, more marketable. Today’s printers are relatively low-cost, have very high quality output, can print in vivid color, and can be operated easily with just a few clicks of a mouse or presses of a button — a far cry from the highly technical, six-step process involved in the early stages of the printer’s development.
Modern printing tech is cutting-edge
Today, modern home printers are leaps and bounds more advanced than their early ’80s counterparts, and it’s rare that you walk into a home without spotting at least one sleek printer perched atop a desk.
STOPPING UNWANTED CALLS
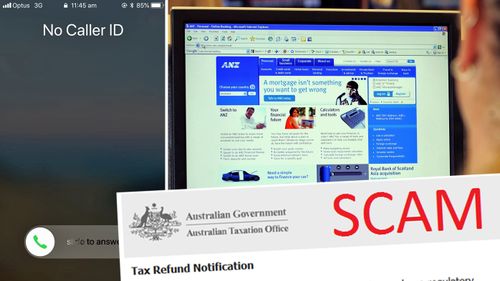
We all know that feeling of having missed from strange numbers you don’t know.These phone calls are often from scammers who now have the ability to mask their spam with local, genuine-looking phone numbers in attempt to steal your money or personal information.Thankfully there are a few ways you can fight back against those random, suspect numbers.
BLOCK INDIVIDUAL NUMBERS ONE BY ONE
This won’t stop you getting harassed by robocalls and spammers, but you do get the instant satisfaction of knowing a particular number will never be able to call you again.To do this in iOS, head to ‘Recents’, tap the blue information icon to the right of the number you want to block and tap ‘Block this Caller’.
For Android, go to the ‘Recents’ section of the ‘Phone’ app, select the number and choose blockIt’s worth noting that this will only work for numbers that have already called you and will have no result blocking scammers using a private number.
THE NUCLEAR OPTION
You can stop all unwanted calls from ringing your phone by only allowing calls from your contact list. This does mean you could miss a call you likely wanted to catch if the number was not saved, but if you have tried everything else the option is always there.To do this in iOS, go to Settings, then tap on “Do Not Disturb” then select “Allow Calls From” then “All Contacts”.For Android, go to “Setting”, then “Do Not Disturb” then limit calls to your contacts like the iPhone.
BUY A SAMSUNG OR GOOGLE
Samsung’s Galaxy S and Note smartphones automatically flag suspected spam calls with a feature known as Smart Call.When a strange number calls your phone, the device will flag it as safe, suspected spam, or fraud.When it’s unsavoury, you can easily block the call and take further action by reporting it.The Google Pixel has a similar feature which will turn the entire screen red as an easy visual reference not to answer the call whenever a known spammer dials your number.Both features can be turned on in Call Settings, although just don’t expect them to perfect.
JOIN THE DO NOT CALL REGISTER
The Do Not Call Register is a free service where consumers can securely register their home, mobile or fax numbers for free to reduce unsolicited telemarketing calls.However, the registry only covers sales calls, and marketers who abide by it.
USE A THIRD-PARTY APP
Similar to the Samsung and Google feature, several apps also have the ability identifying spam numbers and pre-emptively blocking them.One of the more impressive apps known as Hiya will automatically block problematic numbers and “neighbour scams” – spoofed numbers that look like they are coming from a familiar area code.
Public WiFi Security
In a recent survey, 70% of tablet owners and 53% of smartphone / mobile phone owners stated that they use public Wi-Fi hotspots. However, because data sent through public Wi-Fi can easily be intercepted, many mobile device and laptop users are risking the security of their personal information, digital identity and money. Furthermore, if their device or computer is not protected by an effective security and anti-malware product… the risks are even greater.
Wireless Security tips — to help keep you safe on public Wi-Fi
With coffee shops, hotels, shopping malls, airports and many other locations offering their customers free access to public Wi-Fi, it’s a convenient way to check your emails, catch up on social networking or surf the web when you’re out and about. However, cybercriminals will often spy on public Wi-Fi networks and intercept data that is transferred across the link. In this way, the criminal can access users’ banking credentials, account passwords and other valuable information.
Here are some useful tips from Kaspersky Lab’s team of Internet security experts:
- Be aware
Public Wi-Fi is inherently insecure — so be cautious.
- Remember — any device could be at risk
Laptops, smartphones and tablets are all susceptible to the wireless security risks.
- Treat all Wi-Fi links with suspicion
Don’t just assume that the Wi-Fi link is legitimate. It could be a bogus link that has been set up by a cybercriminal that’s trying to capture valuable, personal information from unsuspecting users. Question everything — and don’t connect to an unknown or unrecognised wireless access point.
- Try to verify it’s a legitimate wireless connection
Some bogus links — that have been set up by malicious users — will have a connection name that’s deliberately similar to the coffee shop, hotel or venue that’s offering free Wi-Fi. If you can speak with an employee at the location that’s providing the public Wi-Fi connection, ask for information about their legitimate Wi-Fi access point — such as the connection’s name and IP address.
- Use a VPN (virtual private network)
By using a VPN when you connect to a public Wi-Fi network, you’ll effectively be using a ‘private tunnel’ that encrypts all of your data that passes through the network. This can help to prevent cybercriminals — that are lurking on the network — from intercepting your data.
- Avoid using specific types of website
It’s a good idea to avoid logging into websites where there’s a chance that cybercriminals could capture your identity, passwords or personal information — such as social networking sites, online banking services or any websites that store your credit card information.
- Consider using your mobile phone
If you need to access any websites that store or require the input of any sensitive information — including social networking, online shopping and online banking sites — it may be worthwhile accessing them via your mobile phone network, instead of the public Wi-Fi connection.
- Protect your device against cyberattacks
Make sure all of your devices are protected by a rigorous anti-malware and security solution — and ensure that it’s updated as regularly as possible.
